5 Challenges of Internet of Things ( IOT )
- Security
- Privacy
- Standards
- Regulation
- Development
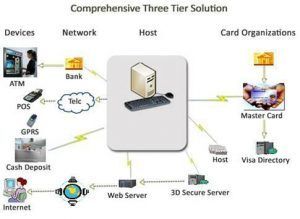
Security Threats in Bank
- Mobile Banking Risks
- Social Networks and Web 2.0
- Malware, Botnets and DDoS Attacks
- Phishing
- ACH Fraud: Corporate Account Takeover
- Cloud Computing
- Inside Attacks
- First-Party Fraud
- Skimming
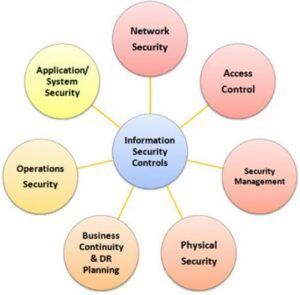
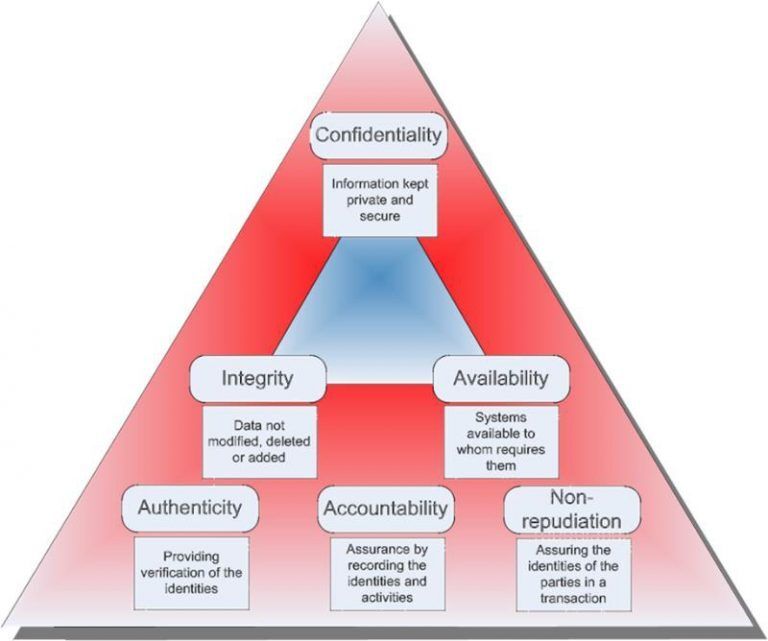
Information Security
Information Security refers to the processes and methodologies which are designed and implemented to protect print, electronic, or any other form of confidential, private and sensitive information or data from unauthorized access, use, misuse, disclosure, destruction, modification, or disruption.
Techniques
- Encryption
- Authentication
- Firewall
- Other Security
- Physical Security
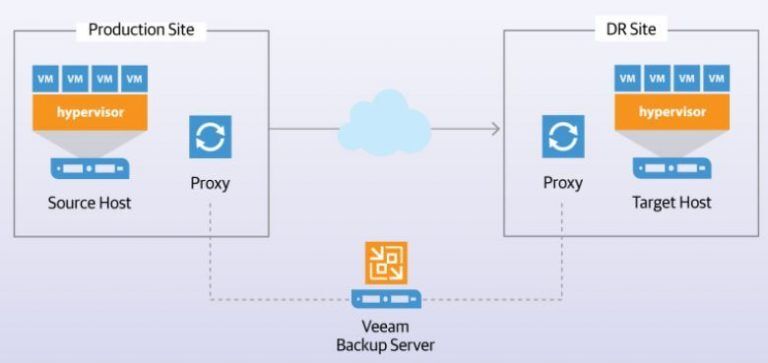
- Data Backup
- Establishment of DR
- Usage of Security Applications
- Usage of Digital Signature
Encryption
Encryption is the conversion of electronic data into another form, called cypher text , which cannot be easily understood by anyone except authorized parties.
Authentication
The process or action of proving or showing something to be true, genuine, or valid .
Types:
- User Authentication
- Machine Authentication
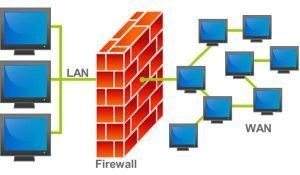
Firewall
A firewall is a network security system, either hardware or software based, that uses rules to control incoming and outgoing network traffic.
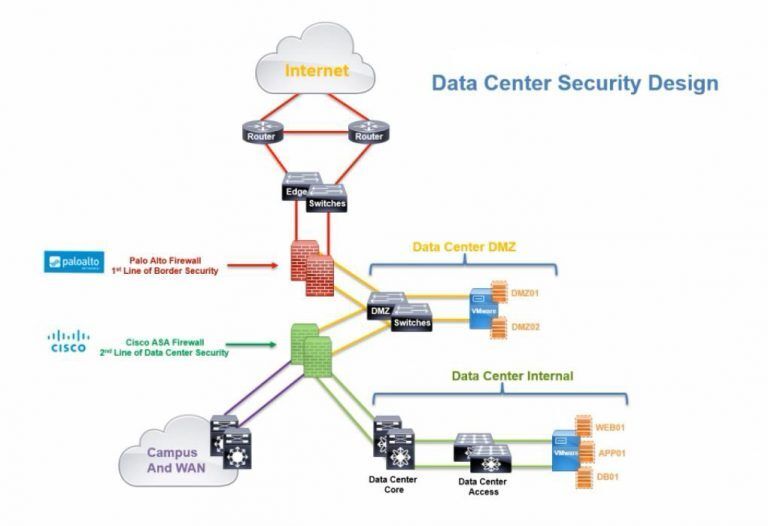
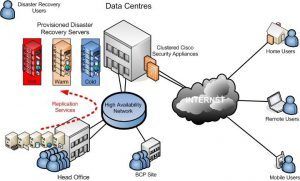
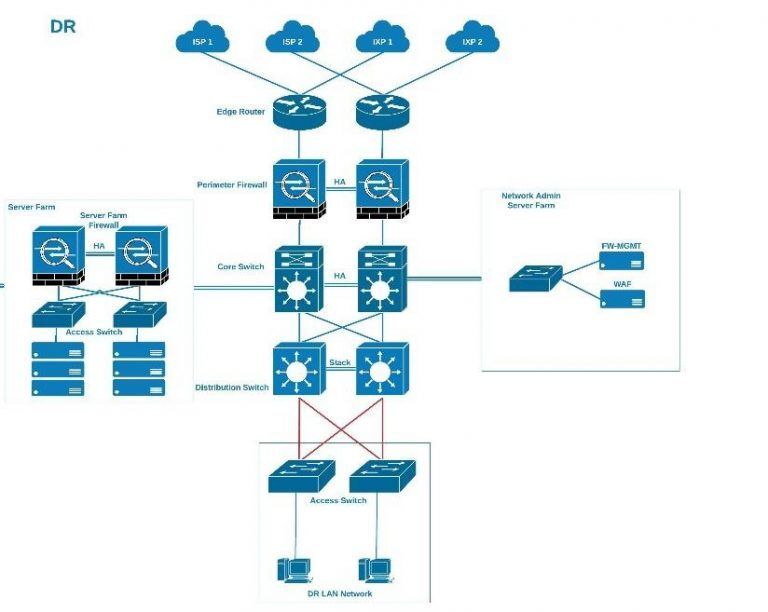
Data Center Security Design
Data Centers
Some Questions
What is Information Security? What are the techniques of Information Security?
Why it is required to maintain multilevel security in bank?



Oldest comments (0)